Docker made containers the standard for application delivery, but teams now face stricter security expectations and closer alignment with Kubernetes. That shift pushed Podman into the spotlight, not as a clone, but as a fundamentally different platform built around rootless operation and a daemonless architecture.
For engineers already deep in Docker workflows, the real question isn’t “what is Podman?” It’s how its architectural model changes isolation, compliance, and day-to-day container management. Those differences matter when you’re securing CI runners, managing multi-tenant Linux systems, or preparing environments for production-grade Kubernetes.
This guide focuses on the practical podman vs docker differences, so you can decide where Docker is still the default and where Podman offers a more secure, modern fit.
Podman vs Docker at a Glance
Before diving into deeper technical details, it helps to see how Docker and Podman differ at a high level. Both engines support containerized workloads, but their philosophies, architectures, and operational models diverge sharply. This quick comparison frames the key contrasts that inform the rest of the discussion.
| Context | Docker | Podman |
| Core Architecture | Client-server model built around the Docker daemon that manages containers, networks, and volumes. | Fully daemonless; each container is its own process, managed directly through libpod. |
| Privileges & Security | Traditionally root-based; rootless mode exists but is still tied to daemon behaviour. | Rootless by design, reducing attack surface and aligning with strict security/compliance requirements. |
| Kubernetes Alignment | Strong Compose ecosystem; Kubernetes support via extra integrations. | Pods are native; can generate Kubernetes YAML directly, making it closer to K8s concepts out-of-the-box. |
| Tooling & Ecosystem | Mature ecosystem, polished Docker Desktop, and unmatched community adoption. | Rapidly growing tooling; integrates with Buildah, Skopeo, and systemd for Linux-native workflows. |
| Performance & Footprint | Slight overhead due to daemon, but stable and highly optimized. | Lighter in many scenarios; faster startup in high-density or CI environments due to daemonless model. |
| Best Fit | Teams wanting simplicity, cross-platform tooling, and the most frictionless onboarding. | Security-sensitive, Linux-first, Kubernetes-centric, or multi-tenant server environments. |
What Docker and Podman Actually Do?
Even though this guide avoids beginner definitions, a short refresher helps clarify why the two engines evolved in such different directions. Docker and Podman solve similar problems, but they approach container building, execution, and lifecycle management differently based on their underlying design.
Docker
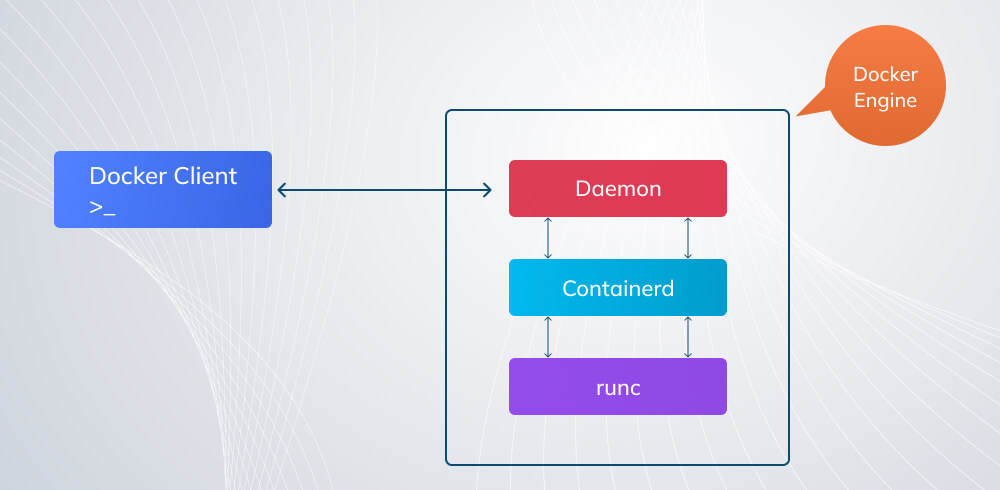
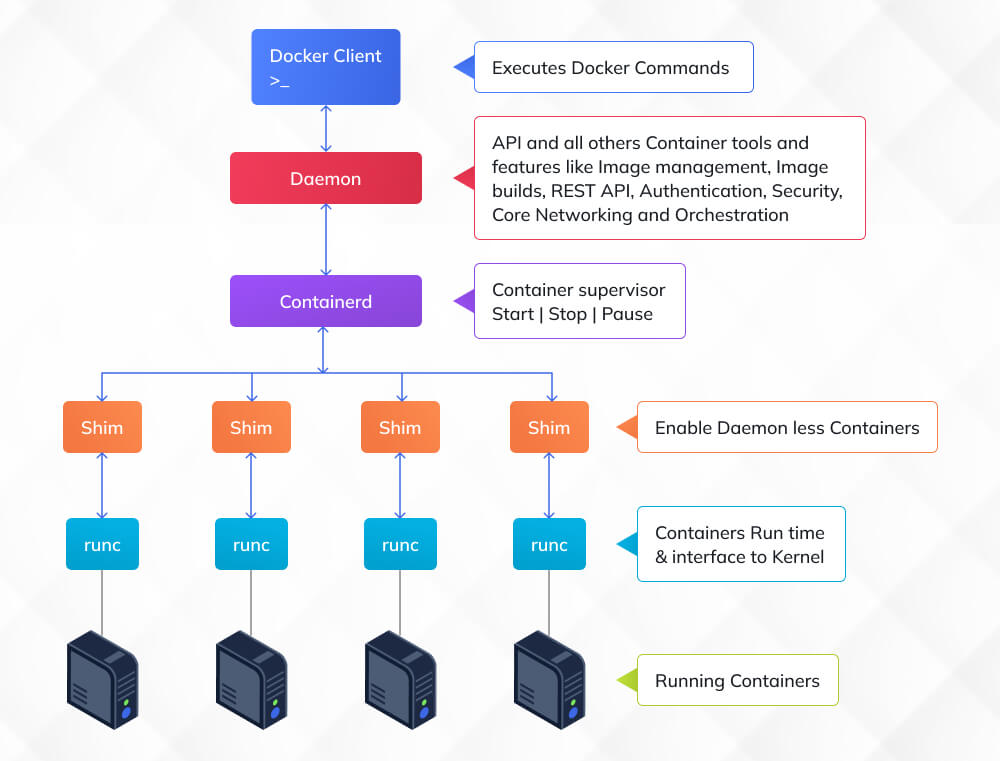
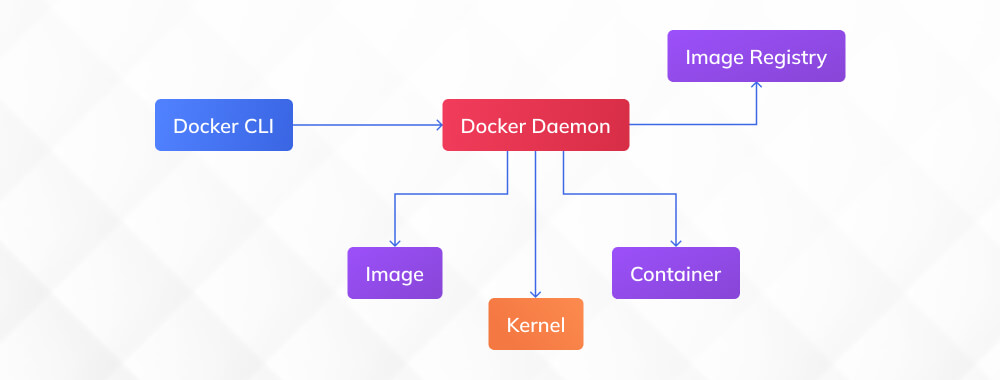
Docker popularised containers through a client-server architecture where the Docker CLI communicates with the dockerd daemon responsible for building images, orchestrating containers, managing networks, and handling volumes.
Its strength comes from a tightly integrated ecosystem, Docker Engine, Docker Desktop, Docker Hub, and Docker Compose. This makes setup, cross-platform development, and team onboarding consistently smooth.
For most organisations, Docker remains the fastest path to a working, standardized container workflow.
Podman
Podman is a daemonless, OCI-compliant container engine built around rootless operation, direct process management, and a pod-native model similar to Kubernetes.
Instead of relying on a long-running root daemon, Podman interacts with the container runtime through libpod, giving each container its own process tree and reducing privilege requirements.
It integrates naturally with Buildah, Skopeo, and systemd, making it a strong fit for security-conscious, Linux-first, and Kubernetes-aligned environments.
Architectural Differences of Docker and Podman
Architecture is where Docker and Podman diverge most significantly. Their internal design decisions directly shape their security posture, reliability, and operational behaviour. Understanding these differences is essential for making an informed choice.
Daemon vs Daemonless Execution
Docker relies on a central service, dockerd, to manage containers, networks, and images. This daemon becomes the single point through which all container operations pass. If dockerd stalls or crashes, the entire container stack becomes inaccessible, even if individual containers were functioning normally. It also means every user’s container activity routes through the same privileged background process, which carries operational and security implications.
Podman removes the daemon entirely. Each podman run command spawns containers as direct child processes of the user invoking them. There is no long-running service to monitor, restart, or patch, and no global process that bottlenecks or centralises control. For teams running containers in multi-user Linux environments or environments enforcing strict privilege separation, this architecture is more predictable, more inspectable, and significantly less fragile.
Root-Based vs Rootless by Design
Docker was historically tied to root access because the daemon needed elevated privileges to manage container namespaces, cgroups, and storage layers. Rootless mode was added later, but it still operates within a design philosophy built around a privileged daemon. As a result, certain features may require workarounds or additional configuration when running Docker in fully rootless contexts.
Podman inverts this model. It treats rootless execution as the default, mapping “root inside the container” to an unprivileged user ID on the host. This limits the blast radius of container compromises and aligns with least-privilege principles common in regulated or sensitive environments. In practice, Podman’s rootless-first design means fewer exceptions, fewer elevated operations, and smoother compliance conversations during audits.
Pod-Native Design vs Compose-First Workflows
Docker focuses on single containers and uses Docker Compose for multi-container definitions. While Compose works well for development and simple deployments, it is not conceptually aligned with Kubernetes pods. Podman, by contrast, treats pods as first-class citizens multiple containers sharing namespaces, networking, and lifecycle by design.
This matters because it brings local container workflows closer to how real-world Kubernetes clusters behave. With podman generate kube, a running pod can be exported into Kubernetes YAML that forms a realistic starting point for deployment manifests. For teams containerising applications destined for Kubernetes, Podman reduces translation overhead and makes local behaviour more faithful to cluster behaviour.
Systemd Integration and Linux-Native Operations
Running containers as system services is common on Linux servers, but Docker traditionally requires workarounds such as wrapper service files or reliance on Docker’s restart policies. Podman, however, can automatically generate systemd units using podman generate systemd, allowing containers or pods to be managed like any other Linux service.
This enables more predictable server behaviour, finer-grained lifecycle control, and cleaner integration with hardened Linux environments. For organisations standardising on systemd across fleet operations, Podman fits the native service model without bending the system around a daemon.
Developer Experience and CLI Compatibility
Despite their architectural contrast, Docker and Podman feel surprisingly similar from the command line. But underneath the familiar syntax, their workflows behave differently. This section focuses on what developers encounter day-to-day: CLI compatibility, Compose behaviour, desktop tooling, and ecosystem support.
CLI Similarity and Migration Ease
Podman intentionally mirrors Docker’s command structure, which is why most teams experimenting with it begin by aliasing docker to podman. Core commands: run, ps, build, logs, exec, pull, push, behave nearly identically, making the transition trivial for day-to-day tasks. But “familiar” does not mean “identical.” Some Docker-specific flags, Compose behaviours, and daemon-dependent workflows don’t translate perfectly because Podman’s architecture fundamentally differs.
For developers, this means the learning curve is minimal, but the migration requires awareness: Podman is compatible enough to feel natural, but strict parity is not its goal.
Docker Compose vs Podman’s Multi-Container Options
Docker Compose still offers a smoother experience for multi-container development. It is widely adopted, supported across tooling, and deeply integrated into Docker Desktop. Podman supports Compose through podman compose, but this compatibility is an additional layer rather than a native design choice.
Podman’s real strength in multi-container setups comes from its pod model, which mirrors Kubernetes’ grouping of containers. For applications destined for Kubernetes, defining workloads with pods is a more accurate representation of production behaviour than Compose-based setups. Developers concerned with long-term maintainability and cluster parity gain more from Podman’s approach, even if Compose remains the faster option for quick prototypes.
Desktop Tooling and Cross-Platform Experience
Docker Desktop remains unmatched in polish on Windows and macOS. It bundles Docker Engine, Kubernetes support, Docker Compose, a built-in UI, and extensive integrations. It removes the friction of configuring virtual machines and abstracts away host-specific quirks, a convenience Podman can’t currently match for non-Linux developers.
Podman Desktop is improving rapidly and provides a cleaner path for Linux-first teams who prefer open-source, daemonless tooling. However, on macOS and Windows it still relies on virtualized environments and lacks the refinement and ecosystem maturity of Docker Desktop. That’s not a flaw; it reflects Podman’s priorities: production realism and rootless security over onboarding convenience.
Tooling Ecosystem and Community Support
Docker’s ecosystem is broader, richer, and more “batteries included.” Tutorials, CI integrations, third-party GUIs, language-specific SDKs, and cloud platform guides overwhelmingly default to Docker. This gives Docker a significant advantage for teams hiring junior engineers or relying on rapid onboarding.
Podman’s ecosystem is more intentional than sprawling. It integrates tightly with Buildah for builds, Skopeo for image operations, and systemd for service orchestration. The tooling is lean, modular, and security-aware, a better fit for teams who want a more controlled environment instead of a monolith that solves every use case by default.
When Docker Is the Better Choice
Choose Docker when your priority is smoothness, onboarding speed, and ecosystem depth. If your team spans Windows, macOS, and Linux, Docker Desktop delivers a consistent environment without forcing developers to fight virtualization layers. Its tight integration with Docker Compose makes local multi-container development straightforward, and its dominance in documentation, CI plugins, SDKs, and tutorials keeps friction low for hires and contractors.
Docker is also the safer option for organisations that want flexibility across cloud platforms. When nearly every tool, guide, and example assumes Docker, choosing it minimizes surprises and accelerates delivery. For large teams that depend on predictable workflows and easy knowledge transfer, Docker remains the default for a reason.
| JaneTech Case Study
JaneTech, a New York–based engineering firm, partnered with Docker to streamline development, improve scalability, and support its diverse portfolio across media, education, gaming, and VR. By standardizing workflows with Docker containers, JaneTech eliminated environment discrepancies, reduced deployment errors, and accelerated setup times. Docker enabled seamless migration across AWS Lambda, ECS, Fargate, Kubernetes, and other cloud services, supporting over 1,800 concurrent container instances and hundreds of thousands of requests during peak usage. With 35+ core services and 50+ optimized Docker images, JaneTech now delivers consistent, enterprise-grade applications with stronger reliability and future-proof flexibility. CTO Mona Fawzy calls Docker “a universal language” that empowers the team to build long-lasting, scalable solutions for enterprise clients. |
When Podman Is the Better Choice
Choose Podman when security, isolation, and Linux-native control matter more than convenience. Its daemonless, rootless-first architecture is inherently aligned with organisations operating under strict compliance, zero-trust principles, or multi-user server environments. If you maintain hardened Linux fleets, research clusters, or shared CI runners, Podman reduces the risk surface without additional wrappers or exceptions.
Podman’s pod-centric model also makes it a natural fit for Kubernetes-bound applications. When developers work locally in pods and export configurations directly into Kubernetes YAML, the development-to-deployment gap becomes much smaller. For teams invested in Linux-first, Kubernetes-heavy workflows, often in enterprise infrastructure, Podman simply maps better to how production operates.
| Podman Case Study
At the SEI, an intern team used Podman at the heart of a DevSecOps example case, redesigning an internal reporting app and its CI/CD pipeline. Instead of jumping straight to features, they focused on a minimum viable process, defining stages, tools, and security safeguards first. Their five-stage pipeline (static analysis with SonarQube, Podman-based image builds, SBOM generation and analysis, secure signing with Cosign, and pushing signed images to the registry) showed how Podman-in-Podman can replace Docker-in-Docker with a more secure, daemonless model. The project improved visibility into vulnerabilities, enforced signed, traceable images, and aligned development, security, and operations around a shared pipeline. Podman enabled container builds that were portable, secure, and well-suited to modern DevSecOps practices. |
Situations Where Using Both Docker and Podman Makes More Sense
The decision does not always have to be binary.
Some mature engineering organisations deliberately use Docker for development and Podman for CI or production.
- Developers get Docker Desktop, Compose, and the ecosystem benefits.
- CI runners use Podman to run rootless containers with reduced blast radius.
- Production stays aligned with Kubernetes concepts by using Podman pods as the local abstraction.
This hybrid model combines Docker’s convenience with Podman’s security posture without forcing teams into a single operational philosophy.
Conclusion: Start From Your Constraints, Not the Tool
The right engine depends on what constraints matter most:
- If you prioritise onboarding, compatibility, and developer experience → Docker.
- If you prioritise security boundaries, Linux-native workflows, and Kubernetes realism → Podman.
- If you need both, use each where it fits instead of forcing a single choice everywhere.
The strength of modern DevOps is not loyalty to tools; it’s the ability to choose architecture over habit.
If your team is looking to strengthen its understanding of CI/CD, containerisation, and cloud-aligned DevOps practices, exploring Invensis Learning’s DevOps Master Certification, AWS DevOps Training, or Azure DevOps Training can provide the structured guidance needed to turn these concepts into production-ready capability.