The term “Hacking” has been part of the computing world for decades and it covers a wide array of topics. Hacking concept fears down people as they think of losing all the vital information stored in the systems. In this post on the Ethical Hacking tutorial, I will explain the types of Ethical Hacking and its importance along with the Ethical Hacking Process
In today’s highly protected era, computers have become an integral part of every business. Networking one system with other systems will help to communicate, which makes hackers steal sensitive information. Globally, organizations are losing millions of income every year. Keeping this in mind, organizations are taking every precautionary measure to safeguard themselves from falling prey to cyber-attacks.
Let’s start this blog on Ethical Hacking tutorials by understanding the definition of Hacking.
Hacking Definition
Hacking is the process of identifying the weakest point within the computer network to acquire illicit access to the organization’s essential information. This could lead to the loss organization’s valuable data, network, or even finances as well. Hacking has become a significant concern with the advent of technology.
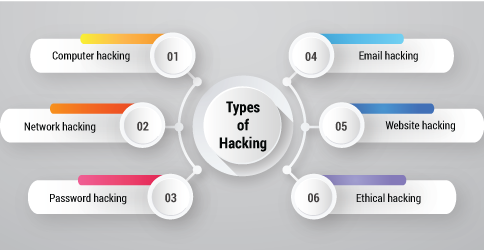
Types of Hacking
Hacking can be categorized into various types based on the reason it is used. Here are a few of them:
Computer Hacking
Computer hacking process involves stealing systems ID and passwords to get illegal access to the organization’s information.
Network Hacking
Network hacking is all about gathering information about the networks to harm the network and business operations.
Password Hacking
Password hacking process involves storing passwords on the computer.
Email Hacking
Email hacking involves getting illegal access to one’s email account without the user’s consent.
Website Hacking
Website hacking is all about getting unauthorized access to the website server, databases, and other interfaces.
Ethical Hacking
Ethical hacking is all about finding computer weaknesses and getting the issue fixed.
Ethical Hacking Definition
Ethical hacking identifies vulnerabilities in a system and systematically resolves them before it gets worse. The hacking process involves the word consent, which discerns from other hacking techniques.
Ethical hacking is all about analyzing the enterprise’s security plan by a team of professionals, who are also known as” White hat hackers”. Their main aim is to penetrate the system to fix the vulnerabilities with prior permission from the client/organization and present a scorecard indicating the chances of risk. Public and private firms and banks usually hire ethical hackers to avoid cybercrimes.
Importance of Ethical Hacking
Regardless of the organization type, you may have to deal with web applications for day-to-day business activities. Considering the organization’s perspective of safeguarding valuable assets/ data, the apt choice is to go for ethical hacking.
Despite the ever-growing demand for ethical hackers globally, many individuals are still worried about security threats.
Here are a few reasons why ethical hacking is worth considering:
- Though the prime purpose of implementing ethical hacking is to prevent sensitive information from into prey’s hands, it also improves digital network security through real-world testing.
- Ethical hacking helps you to identify potential entry points from hackers and fix it a timely.
- Considering an employment perspective, ethical hacking helps to upskill your knowledge to get into various job roles such as quality assurance tester, software developer, risk management, etc.
- In addition to protecting the organization’s valuable information, it also prevents cyber-terrorism, ensuring the nation’s safety.
- Ethical hackers are the major strength of the organization. They work with quality analysts and perform quick security tests under all conditions to check whether the software functions aptly.
Next in this Ethical Hacking tutorial, let’s understand what are the skills required to become an Ethical Hacker.
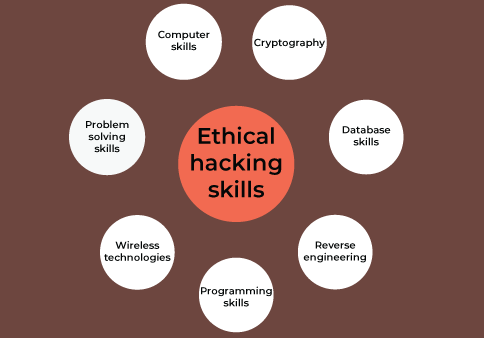
Skills to Consider
Ethical hacker identifies the essential loopholes within a network or a system or any applications and reports them to the concerned departments. Let’s understand the essential skills to become an ethical hacker:
Computer Skills
Computer skills seem like basic ones, but one of the most vital skills to consider. Having thorough knowledge and ability to handle operating systems, networking parameters, windows operating software, and related technology is essential.
Cryptography
The cryptography concept converts the textual message into a non-readable format, making it inexplicable for hackers to decode it. An ethical hacker uses cryptography to keep communication between employees safe and secured.
Database Skills
DBMS is the core of managing all the databases. Illegal access to the organization’s sensitive information can cause a tremendous threat to the organization. That’s why an ethical hacker should possess knowledge of various data schemas and database engines, which in turn helps the organization develop a robust database management system.
Reverse Engineering
Reverse engineering ensures that the system is free of security flaws and vulnerabilities. It also makes the system robust by safeguarding the organization’s vital information from spyware and hackers. Reverse engineering helps to improve the system’s understandability and helps to prepare necessary documents as well.
Programming Skills
The programming skill is one of the essential skills to consider. The word” Programming” involves writing code to perform various activities. Here are a few programming languages for ethical hackers C, C++, SQL, PHP, Ruby, Perl, and so on.
Wireless Technologies
Ethical hackers use wireless technologies such as WPA, WPS, WEP, etc., to safeguard the systems from sharing sensitive information through an invisible source.
Problem-Solving Skills
In addition to the above-mentioned technical skills, an ethical hacker should be a proactive problem solver and possess exceptional thinking capability. They must be aware of all the essential techniques to check security breaches.
I hope you have enjoyed reading this Ethical Hacking tutorial blog so far, next, I will explain the entire process involved in Ethical Hacking.
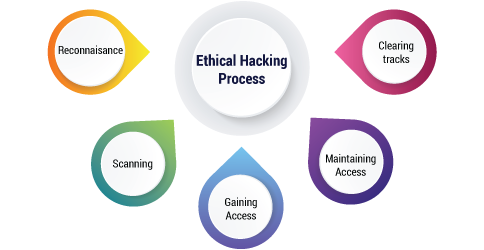
Ethical Hacking Process
On categorizing ethical hacking into six phases that help hackers go for a structured hacking process. They are as mentioned below:
Reconnaissance
The reconnaissance phase is also known as the footprinting and information gathering phase. Here, an ethical hacker can gain valuable information about the organization, which includes collecting old passwords and employee names through active or passive techniques.
Footprinting is categorized into two types:
Active – Direct interaction to collect information about the target
Passive- Trying to gather information about targeting without direct access.
Scanning
The scanning process involves collecting active information from a network or a target system for issues which can be easily exploited. A few of the tools used for the scanning process are Nexpose, NMAP, and Nessus.
Gaining Access
At this phase, the hacker has all the essential information required to carry out the attack using various tools and methods.
Maintaining Access
Maintaining access is one of the essential steps. Even if the hacker restarts/shut down the system, the connection remains the same. This phase involves getting access to the target until he finishes the accomplished task.
Clearing Tracks
The final step in the ethical hacking process is to clean all the hacking traces as no thief wants to get caught red-hand. The process involves modifying/deleting the logs, deleting the folders, and uninstalling the applications.
Conclusion
I hope you have enjoyed reading this post on Ethical Hacking Tutorial. The need for ethical hackers has gained prominence globally with the surge in security threats. Incorporating a robust approach to implementing security policies would surely help organizations shield their sensitive information and fine-tune the gaps that lead to the compromise of the organization’s security.
Businesses operate in a structured and complex environment involving security policies, prevailing technologies, and interactions. Thus, accessing the systems holistically and organizational security must be monitored regularly for its efficiency.
Professionals aspiring to start a career in ethical hacking can upskill their knowledge with industry experts at Invensis learning. A certification in ethical hacking will help the individuals to get trained on ethical hacking with skills and expertise to safeguard their interests in the same field.