Ethical hacking has become a knight in shining armour in the world of cybercrime. While cyberattacks remain rampant across organizations, across industries, and the world, ethical hacking gives companies the solution to help them combat this ever-growing problem. There are different phases of ethical hacking.
IT security conditions are so dire that, more often than not, it takes up to 6 months for organizations to realize that there has been a breach. This is why they need to work with ethical hackers to upgrade their cybersecurity measures and safeguard their data. Organizations need top-notch security measures to combat the level and the sheer number of attacks that take place on a daily basis. A cyber attack has been said to occur every 39 seconds, and age-old systems are not equipped enough to handle them all. Regular updates and upgrades to the IT security systems are the best way to protect companies against this growing problem.
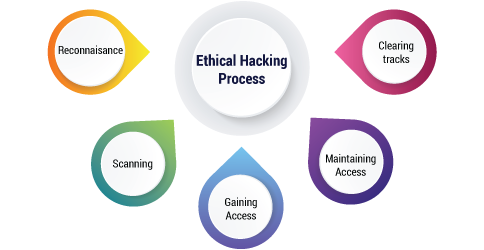
What Are the Different Phases of Ethical Hacking?
Organizations employ ethical hackers to simulate a real cyberattack on their systems and networks. This attack comes in different phases. It takes a lot of skill and effort for ethical hackers to identify all the vulnerabilities and exploit them to their full benefit. This simulated attack is used to pinpoint all areas of weaknesses that the organization faces to work towards strengthening them. The phases of ethical hacking are:
- The Reconnaissance Phase
- The Scanning Phase
- The Gaining Access Phase
- The Maintaining Access Phase
- The Covering of Tracks Phase
The Reconnaissance Phase
This is the first stage in the ethical hacking process. The white-hat hacker collects all the information available about the networks and systems in place, as well as the security measures that have been implemented. The ethical hacker has two types of reconnaissance that he can do in this phase. These are:
- Active reconnaissance
- Passive reconnaissance
Active reconnaissance is looking for information about the target network system, server, or application to increase the chances of the hacker being detected in the system. It is a lot riskier than the second type of reconnaissance, which is passive reconnaissance. Passive reconnaissance is the stealthier way of gaining information about the target. This is focused on information gathering about the company’s key members, essential facts about the company, finding out its IP addresses, and looking for other types of critical information about the company.
Since most organizations have nearly all their information public, passively gathering information can be very easy for an ethical hacker.
The Scanning Phase
The second phase in an ethical hacker’s strategy is the scanning phase. This step involves using all the information obtained in the reconnaissance phase and applying it to look for vulnerabilities in the targeted area. There are different types of scans done by ethical hackers. They can scan for open ports or different services that are running unprotected in the organization.
Ethical hackers can also perform vulnerability scans to find weaknesses in the company servers, which can be exploited. This process has become automated because there are many tools available for hackers to perform vulnerability scans. White hat hackers can also create various ‘maps’ of networks. This process of network mapping includes finding the firewall used by the organization and different routers and networks to help them during their hacking process.
The Gaining Access Phase
This is where the ethical hacker does the actual hacking. He uses all the information obtained and analyzed from the previous two phases to launch a full-fledged attack on the system or network the ethical hacker is trying to infiltrate. He exploits all the exposed vulnerabilities and gains control of the system he has hacked. Now the hacker can steal all the data he has available on hand, corrupt the systems, add viruses or other malicious entities, or manipulate it to his/her benefit.
Maintaining Access Phase
Usually, hackers have a mission to accomplish or a plan to follow when they hack into an organization’s system. This means just breaking into or hacking into the system is not going to be enough. The ethical hacker has to maintain his access to the server until he fulfills his goal. Ethical hackers usually employ Trojans and other backdoors or rootkits to accomplish this phase. They can also use this maintaining access phase to launch several other attacks to inflict more damage to the organization.
Covering of Tracks Phase
This is the final step to complete the entire ethical hacking process. If this phase is completed successfully, the ethical hacker has managed to hack into a system or network. He/she could inflict as much damage as possible and has managed to leave the system without a trace. They need to cover their tracks throughout to avoid detection while entering and leaving the network or server. The security systems in place should not be able to identify the attacker. The sign of a successful simulated cyber attack is if the security system never realized that an attack took place altogether.
This includes many of the following measures that an ethical hacker takes to hide and remove his presence completely:
- Deleting all logs
- Corrupting logs
- Modifying certain values of logs or registries
- Deleting all the folders that have been created by the ethical hacker
- Uninstalling all the applications
- Removing all traces of any activity performed by an ethical hacker in the system or network
Final Thoughts
Ethical hacking is a long and difficult process that involves many phases. Working professionals need to have the necessary ethical hacking training skills to become successful ethical hackers. The phases require a lot of time, knowledge, and expertise to accomplish and should be taken seriously. Organizations also opt for certified individuals over their non-certified counterparts because they are in charge of protecting the company’s sensitive data and digital assets.