Information security describes the activities which are related to the protection of information and infrastructure assets against the risk of being misused, lost, disclosed, and damaged. Information Security Management (ISM) is a governance activity within the corporate governance framework. ISM describes the controls which are necessary to be implemented by an organization to make sure that is sensibly managing the risks. The main purpose of ISM in ITIL is to align IT security with business security and make sure that it matches the required needs of the business.
The Objective of Information Security Management in ITIL
The objectives of ISM are to ensure that:
- Information is available and ready to use whenever it is required.
- The systems which provide information can resist attacks adequately and recover from failures/prevent them.
- The information is visible or disclosed to only those people who have the necessary clearance and have the right to know.
- The information is complete, accurate, and has complete protection against modification by unauthorized personnel.
- The business transactions and exchange of information between enterprises or partners are trustworthy.
Scope of Information Security Management in ITIL
Things such as data stores, databases, metadata, and all the channels used to exchange that information. It raises awareness all across the organization regarding the need to keep all the information assets safe. ISM should understand the following:
- The plans and policies of business security.
- The present operations the business and security requirements.
- The plans and requirements of the business for the future.
- The legislative requirements.
- The responsibilities and obligations regarding security are contained in the service level agreements.
- The risks in business and IT and their management.
Value of Information Security Management in ITIL
Implementing Information Security Management in an organization imparts a lot of benefits such as:
- Ensures that the information security policy is maintained and enforced properly such that the needs of the business security policy and corporate governance are fulfilled.
- It helps to protect all forms of information such as the ones which are digitally stored on devices and the cloud, paper-based, company secrets, and intellectual property.
- Increases the resistance to cyber-attacks and malware if implemented properly.
- It provides a framework for keeping all the information safe which is managed from one place.
- Adapts to constant changes in the threat environment and reduces the security threats which are constantly evolving.
- It helps to reduce the costs which are associated with information security by adding only the protection layers which are necessary and removing the redundant ones.
Basic Concepts of Information Security Management
The following basic concepts are necessary to understand Information Security Management.
Information Security Policy
The information security policy needs to have complete support and commitment from the senior-level IT and business management in the organization. It should have under its purview all the areas of information security and the appropriate measures to meet the objectives of Information security management.
Explore the blog to understand how an Information Security Analyst plays a critical role in creation of the information security policy!
Risk Assessment and Management
It is vital to have a formal risk assessment and management policy that is related to information security and processing. It often collaborates with the business, It service continuity management, and availability management in order to perform risk assessments.
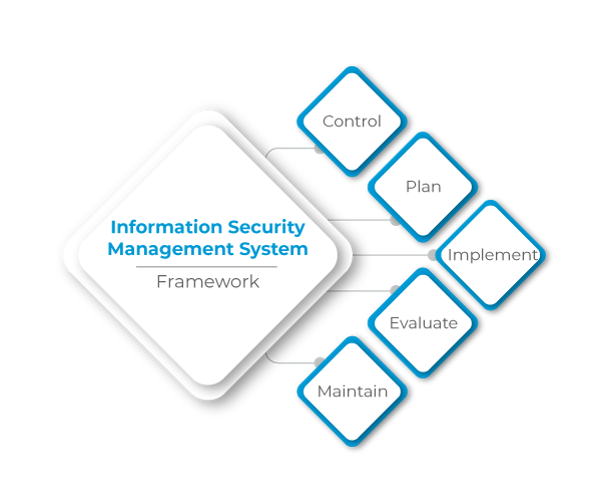
Information Security Management System
The system forms the basis for developing a cost-effective program for information security that supports the objectives of the business. It focuses on the five key elements which are control, plan, implement, evaluate and maintain. Organizations can seek independent certification of their Information Security Management against the ISO/IEC 27001 standard.
The Framework of Information Security Management in ITIL
There are five key elements that are addressed in an Information Security Management system framework.
1. Control
A management framework should be established to manage information security, prepare and implement a policy, allocate responsibilities, to establish and control the documentation.
2. Plan
This phase of the framework involves the collection of information and understanding of the security requirements of the organization. Afterward, the appropriate solutions should be recommended keeping in mind the budget and corporate culture.
3. Implement
In the implementation phase, the plan will be put into action. While doing so, it is important to ensure that adequate safeguards are in place to enact and enforce the information security policy.
4. Evaluate
After the security policies and plans have been implemented, it is necessary to monitor them and make sure that the systems are completely secure and operating in accordance with the policies, security requirements, and service level agreements of the organization.
5. Maintain
For an information management system to be effective, it needs to be improved on a continuous basis. This involves revising the service level agreements, security policies, and the techniques used to monitor and control.
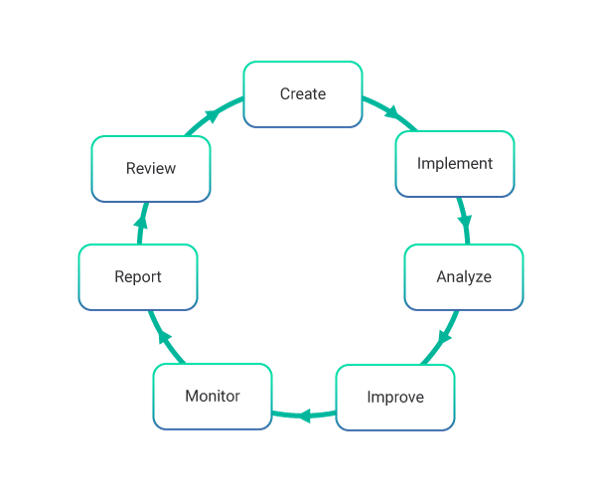
Process Activities of Information Security Management in ITIL
The main activities of Information Security Management are:
- Create, review and revise the information security policy as per the requirements.
- Communicate, implement and enforce the security policies adequately.
- Analyze and classify all the information and documentation in possession.
- Implement a set of security controls and risk responses and improve them.
- Constantly monitor and manage all breaches of security and any major security incidents.
- Analyze, report on, and take the necessary actions in order to decrease the volume and effect of security incidents.
- Schedule and perform security reviews, audits, and penetration tests.
Challenges of Information Security Management
The challenges faced by information security management are:
- It has to ensure that there is adequate support for the information security policy from the business. This is because information security objectives cannot be fulfilled with adequate support and endorsement from top-level management.
- A constantly evolving threat scenario where newer and stronger threats keep popping up.
Risks of Information Security Management
The risks which are encountered by information security management are:
- A lack of commitment from the business to the ISM process.
- A lack of resources or budget for the process.
- Risk assessment is conducted in an isolated manner without combining with availability management and IT Service Continuity Management.
Conclusion
Through proper implementation, it ensures that information is available and ready to use whenever it is required, and the systems which provide information can resist attacks adequately and recover from failures or prevent them. Learn more about such concepts in the ITIL 4 Foundation certification and gain professional expertise in service management to excel in your career.
Know more about Service Management best practices through Invensis Learning’s IT Service Management certification training on ITIL 4 Foundation Online, SIAM Foundation, SIAM professional, VeriSM, etc.